Safeguarding your organization involves more than just setting strong passwords. As cybersecurity threats become more sophisticated, protecting your network, devices, and applications requires both expertise and ongoing vigilance. Canon and its trusted partners are here to help by offering comprehensive Managed Security services designed to proactively defend against external threats and ease the burden on your internal team.
Baseline Security Assessment
Are you confident your current security posture is serving you well?
Are you just beginning your cybersecurity journey?
At Canon, we meet you wherever you are. You cannot manage what you cannot see, and without a clear map, effective control is nearly impossible. So let the Canon Managed Security team give you the lay of the land with our Baseline Security Assessment.
Charting a Course for Success
Ideal for organizations with 10 to 500 employees, the Baseline Security Assessment evaluates your security posture and provides you with a detailed assessment report.

Penetration Testing (PEN Testing)
What is PEN Testing?
PEN testing is an authorized simulation of a cyberattack performed by ethical hackers to identify vulnerabilities in your IT security systems before harmful hackers can exploit them. Uncovering weaknesses early is critical to helping prevent expensive and damaging breaches.
Best Practices for PEN Testing
You can’t protect what you cannot see. PEN testing should be conducted at least once a year, but optimally every quarter—especially in regulated industries where you are likely bound by specific protocols that mandate third-party vulnerability assessments and PEN tests. Additionally, many cybersecurity insurance underwriters have strict requirements that mandate frequent testing.

Types of PEN Testing
We simulate both internal and external attacks by deploying the latest tactics, techniques, and procedures. The penetration tester will attempt to exploit systems and gain access to data. This results in the identification of systemic weaknesses with areas of remediation ranked by criticality and is supported by technical- and executive-level reporting.
Benefits include:
- Testing prevention and detection capabilities.
- Utilizing OWASP and OSSTMM methodologies.
- Validation of external and/or internal security controls.
- Identification of high-risk vulnerabilities.
- Compliance support for HIPAA, PCI 3.x, Cyber Insurance, ISO27001 requirements.
- Credentials include CISSP, CEH, CTPRP, and ITILv3.
Managed Vulnerability Services (MVS)
Let the experts help support you in strengthening your security posture.
A Managed Vulnerability Services (MVS) team is staffed with credentialed professionals that help to continuously identify vulnerabilities across your on-premises and cloud environments. These experts serve as an extension of your InfoSec team, providing analysis and remediation guidance.
Canon’s approach in this area includes:
- Discovery: Executive summaries for non-technical audiences, and detailed summaries for technical audiences.
- Reporting: Monthly internal scans, and weekly external scans.
- Verification: Monitors scans for errors and accuracy.
An MVS team can provide you with guidance and recommendations during the remediation process, along with ad-hoc scanning to help verify that vulnerabilities have been remediated effectively.

Managed Detection and Response (MDR)
Cybersecurity is not just a technical issue. It’s a critical business concern. A crucial component of modern cybersecurity strategies is to include 24/7/365 Managed Detection and Response (MDR) services, which provide organizations with expert monitoring, detection, and response capabilities.
Learn more:
- Management of Existing Endpoint Protection Platform, including (where applicable):
- Security Operations Center (SOC) monitoring detection and prevention services.
- Machine Learning (ML) and Artificial Intelligence (AI)-enabled services to help detect known and unknown malware and ransomware.
- Behavior-based indicators of attack (IOAs) to help prevent sophisticated file-less and malware-free attacks.
- Exploit blocking to help prevent the execution and spread of threats via unpatched vulnerabilities.
- Threat Intelligence prevention of activities known to be malicious.
- SOC investigation and response to detections.
- Continuous raw event recording with full spectrum visibility at the endpoint.
- Enablement of threat hunting—proactive and managed—with full endpoint activity details.
- Provision of entire attack life cycle visibility with context and threat intelligence data.
- Situational awareness on the current threat level of the organization, and how it’s changing over time.
Virtual Chief Information Security Officer Services (vCISO)
Stay ahead of sophisticated threats with a trusted team
Every organization can’t afford a fully staffed security operations center. However, in today’s high-risk workplace environments, neglecting essential security measures can lead to disastrous outcomes.
vCISO
- Audit Backup Process and Retention, and Backup/Restore Testing.
- Incident Response Plan Review.
- IT Security Policy Review.
- Disaster Recover Planning.
- A Monthly Rate: Ongoing vCISO services available, up to 10 hours per month.
- An Hourly Rate: Minimum 10 hours if purchasing standalone.
- Baseline Security Assessment (evaluates organization’s security posture through external vulnerability scan, risk questionnaire, and consultation).

Concierge Services
Empower Your Employees to be Frontline Defenders
Your employees can either be your biggest threat or your best defense. But they do not know what they do not know.
Sixty-eight percent of all breaches include the human element.* Just one employee who clicks on a spear phishing email or uses a USB drive infected with malware can lead to catastrophic loss for your organization. That is why training and awareness for your employees and executives is critical.
68%
of all breaches include the human element.*
*Verizon, 2024 Data Breach Investigations Report
Concierge Security Awareness Training
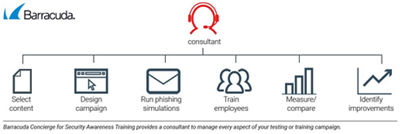
Build a Resilient Workforce with Concierge for Security Awareness Training
Concierge for Security Awareness Training is a service that offloads the tasks of defining, configuring, executing, and analyzing your phishing simulation and training campaigns to a dedicated email security consultant.
Your Concierge consultant can support you with a complete managed service experience. Or you can choose to engage more actively as a partner in creating and executing custom campaigns. The choice is yours.
Concierge at a Glance
- Dedicated security awareness consultant
- Customized simulations and training
- Online training for your administrators
- Strategic campaign-design consultations
- Detailed reporting and analysis

Expert Program Design
Your dedicated Concierge consultant can design high-performance, SCORM (Sharable Content Object Reference Model)-compliant training programs that leverage the latest developments in the field of automated, computer-based learning.
Experienced Program Operation
Your Concierge consultant can help deliver complete, turnkey operation of your campaigns—from beginning to end.
Excellent Program Results
Customers who utilize a Concierge consultant consistently report double-digit phishing awareness improvements across a broad range of departments and employees.
Printer Fleet Cybersecurity as a Service (PFCaaS)
Help Secure Your Devices Against Damaging Cyber Threats
Printers connected to corporate networks are often overlooked and vulnerable. They are rarely configured or updated for security, which can create significant risk. Furthermore, large companies may have hundreds or even thousands of printers of various makes, models, and ages in their fleet.
Canon’s Printer Fleet Cybersecurity as a Service can help address this gap effectively and affordably by:
- Establishing a “Gold Standard” for security settings to meet your organization’s security objectives.
- Implementing automated services to check that these standards are maintained.
- Deploying real-time event and security alert monitoring.
- Supporting asset management and firmware security.
Email Protection
Safeguarding the Email Gateway is Simply Not Enough
Cybercriminals use automation, AI, and other productivity tools to trick users into revealing passwords or installing malware. Security awareness simulation training programs can help to transform your employees from weak links into top-notch defense. A Concierge service can support your organization in relieving the burden of campaign execution, measuring, and reporting—freeing your staff up to focus on high-priority business.
Artificial intelligence-driven email protection solutions can help safeguard your inbox, detect patterns, and mitigate threats before they happen, while also providing cloud backup.
Take the next step in fortifying your email security.
Resources
Managed Vulnerabiity Services - Data Sheet
05.23.25
0.4 MB
Extended Detection and Response XDR - Listicle
05.23.25
5.9 MB
Enhance Your Cybersecurity Posture wih Flexible vCISO Services - Listicle
05.23.25
1 MB
Canon Managed Security - Flyer
05.23.25
0.3 MB
5 Pillars of Security - Brochure
05.23.25
6.7 MB
The Baseline Security Assessment - Flyer
05.23.25
1.5 MB
Barracuda Email Protection - Brochure
05.28.25
1.4 MB
Managed Detection and Response Service Brief
05.28.25
0.4 MB
Canon Managed Vulnerability Services - Flyer
05.28.25
1.4 MB
Canon PEN Testing - Flyer
05.29.25
0.3 MB
Managed Vulnerability Services - Flyer
05.29.25
0.3 MB
Barracuda Security Awareness Training
06.06.25
1.5 MB
Foundational Elements of Security eBook
06.13.25
1.6 MB
The True Cost of Cybersecurity
06.16.25
3.4 MB
Cybersecurity 4 Overlooked Areas and How To Secure Them - listicle
06.16.25
2.4 MB
Are you ready to step up your security? Let’s talk.
Many variables can impact the security of a customer’s device and data. Canon does not warrant that the use of services, equipment, or related features detailed herein will eliminate the risk of potential malicious attacks, or misuse of devices or data or other security issues.



